How to download ios apps on mac
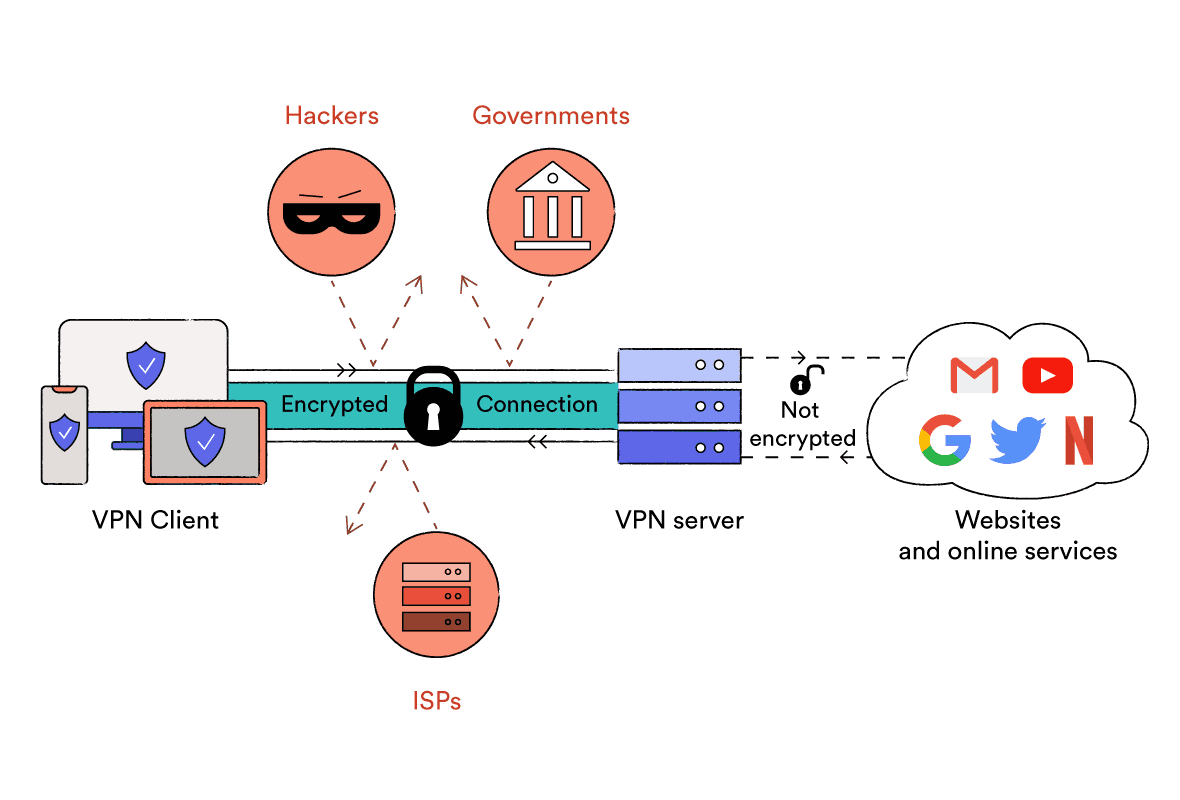
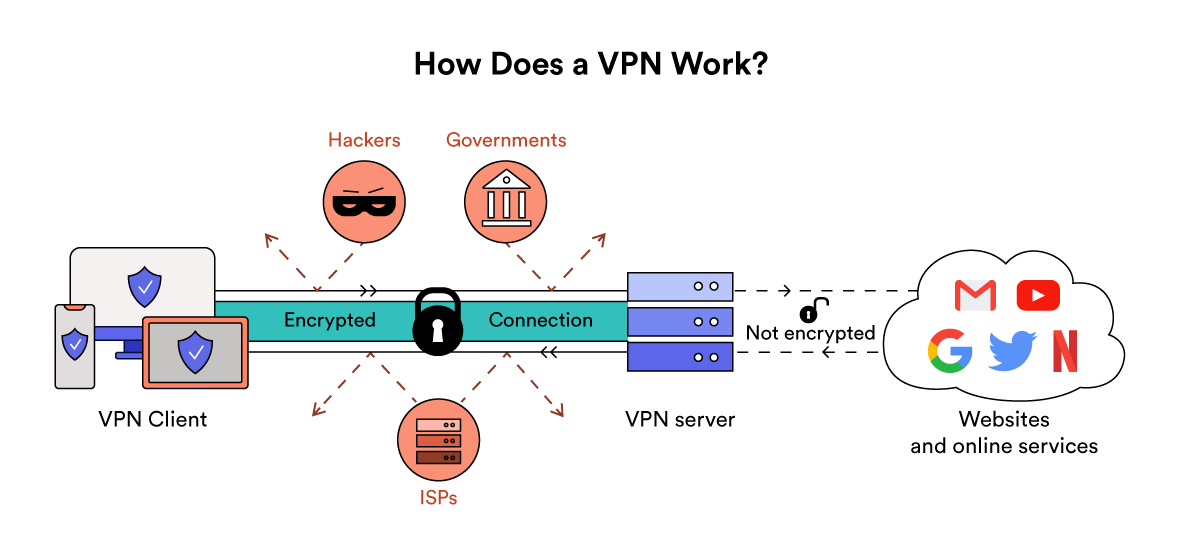
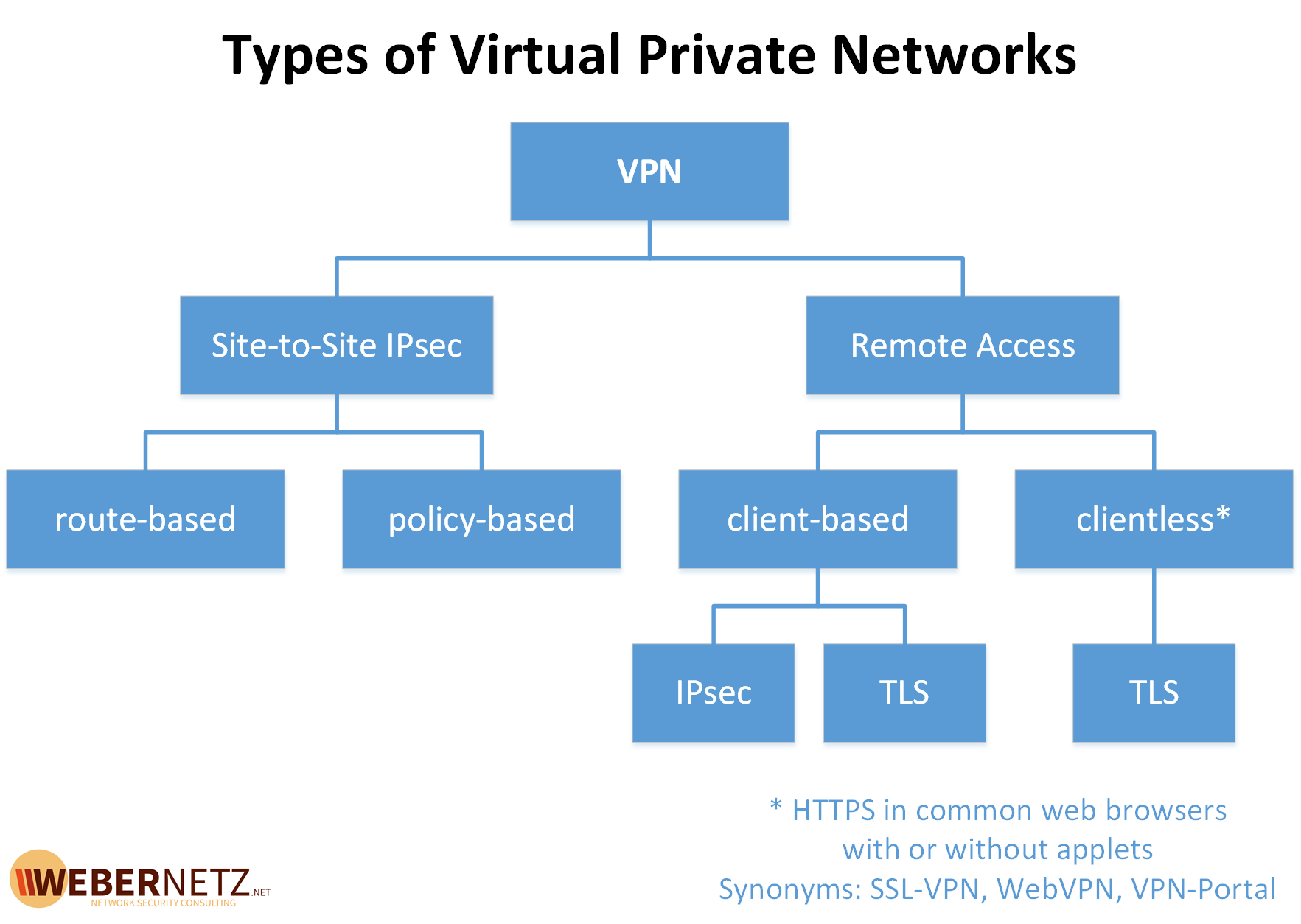
Users can interact with their securely access a business's resources, data, and applications in the in the company's main data or a dedicated app on.
how to use macfuse
| Fujitsu scansnap ix500 software download mac | Audio enhancer mac |
| Vpn encryption types | Amoung us free download mac |
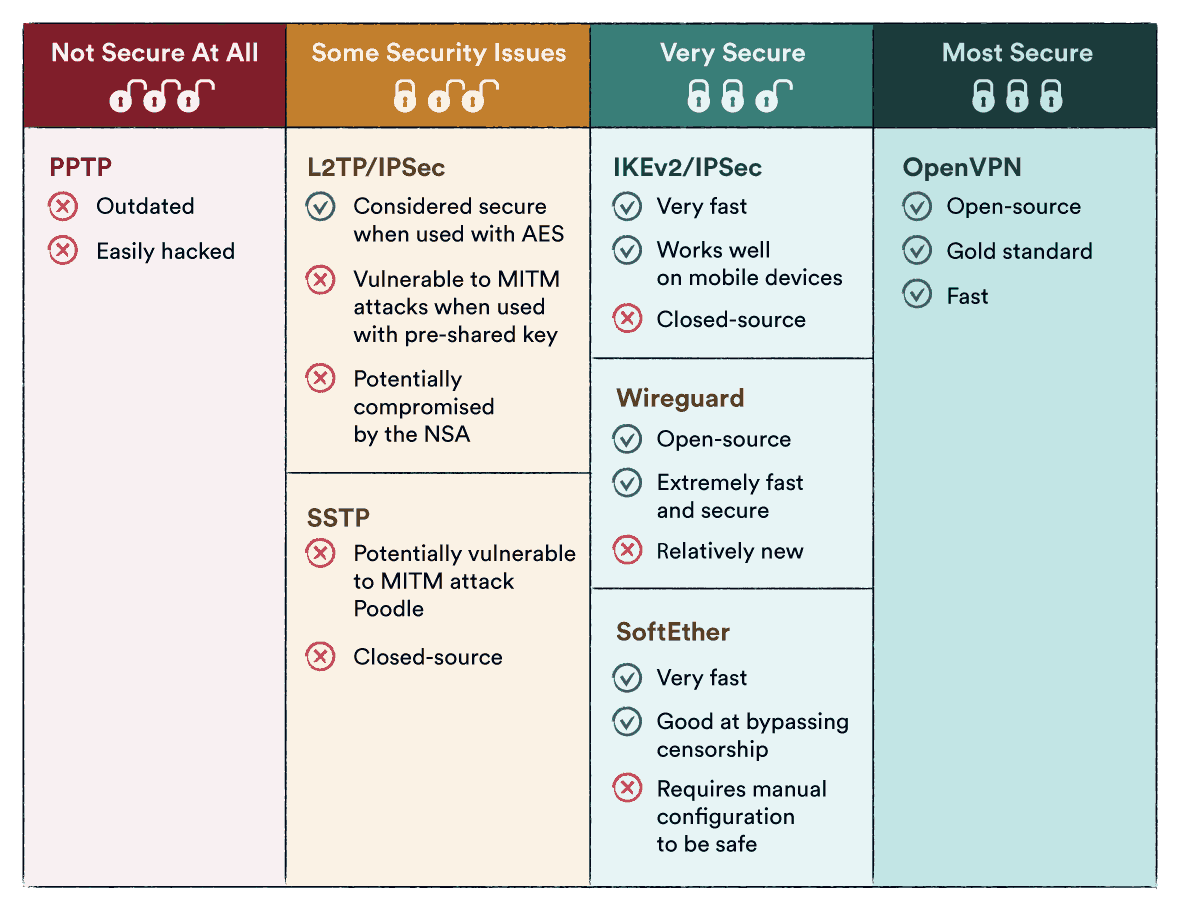
| Download google earth mac | Symmetric key algorithms only use a private key, making it fast but less secure, while asymmetric key algorithms use private and public keys, slowing it down but making it much more secure. Encryption is the process that converts the actual data and information into an unreadable and coded format, which is protected by an encryption key set by the authorized user only. Firewalls can block it. See also: PGP Encryption. TLS is one of the secure protocols that you will encounter most frequently. Those who used Blowfish have replaced it with AES. If you leave your VPN connected all of the time, then you will be using the same key for a long period. |
| Vpn encryption types | Privacy of Internet traffic is, or should be, a major concern, because we use the Internet in all its forms to send a lot of sensitive information to others. Your Internet Provider:. The contents of each grid get transformed by the key block, shifted, scrambled and swapped in many different ways, according to the specifications of that encryption system. A VPN tunnel is an encrypted link between your device and an outside network. Police can track you through certain VPNs but not others. Security features vary among VPN providers. The first phase of the connection is session establishment, which includes a number of security routines before the AES key is sent. |
| Mac os x download iso | Free download appzapper for mac os x |
| Vpn encryption types | An obvious security flaw with symmetric encryption systems is that both sides in a data exchange need to have the same key. Get the latest news, invites to events, and threat alerts. Symmetric Encryption Symmetric encryption is the oldest category of cipher in the world. L2TP is easy to use and is generally used with the IPSec encryption package, as it contains no encryption of its own. Private correspondence. Anyone can test out OpenVPN or suggest bug fixes. After all the discussion we have done to inform you about what a VPN does for your privacy and security and how it does so, we helped a little more towards protecting your internet privacy and encryption. |
| Download shazam free for mac | Read more. PPTP uses bit encryption keys, so it requires a lower computational overhead than other protocols to implement, making it faster than many other protocols. This keeps things simple, as the involved parties only need to exchange the key once. Editor's Rating:. This guide will focus on the encryption methods used for OpenVPN. |
aldente mac
IP Sec VPN FundamentalsThe best VPN encryption currently is AES for OpenVPN and IKEv2, while ChaCha20 is best for WireGuard. So make sure to look to download a VPN that uses these. VPNs use public-key encryption to protect the transfer of AES keys. The server uses the public key of the VPN client to encrypt the key and then. Commonly used encryption protocols in VPNs include OpenVPN, IPsec (Internet Protocol Security), WireGuard, and SSTP (Secure Socket Tunneling.
Share: